Follow-Up Management
The primary target of the FURIA system was initially to provide reliable, comprehensive, flexible and resourceful support of your Audit Follow-Up process, at very cost-efficient TCO levels.
FURIA Audit Reports are entered and treated as complex atoms that contains not only the Audit Findings as atoms, but also all relevant information that you want to store and reuse in your cumulative and drill-down reports. FURIA Audit Reports are system objects that can be fully customized in accordance to your particular format of the standard Audit Reports.
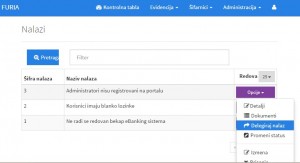
Illustrative example of minimal configuration of the Audit Report stages:
Illustrative example of minimal configuration of the Audit Finding stages:
That means that you can at any time choose and add any of the fields used in your Audit Reports that you find relevant for reviewing and usage in reporting engine: particular audit dates (dates of on-field auditing, report publishing date, date of approval on Management Board and/or Audit Committee, etc.), distributive lists, description sections (audit engagement definition, methodology description, typical audit report introduction sections, Executive Summary, etc.), variety of numeric or other type of metrics (e.g. overall risk value, audit engagement financial and/or man-day costs, charts, etc.), you can attach or reference the relevant documents (you can link the Report with particular laws and regulations, standards, internal processes, or upload any relevant material such as scanned final Audit Report together with formal approvals, or similar), you can set system privileges for access to the Report or its attached documents, and much more.
Examples of different doc classification and docs attached/referenced to the finding:
Each Audit Report is identified with unique ID in accordance with your internal naming convention (example: IAR 01/2015 Card management audit).
After entering all necessary fields and attaching the documents to the Audit Report, you are ready to deal with its functional atoms – Audit Findings. Each Finding-atom consists of typical, common fields used in the modern audits: finding title/caption, expectations, implication, risk type, risk level, the cause, audit recommendation, management response, agreed actions, responsible auditee, deadline and so on.
Example of the typical Audit Finding structure: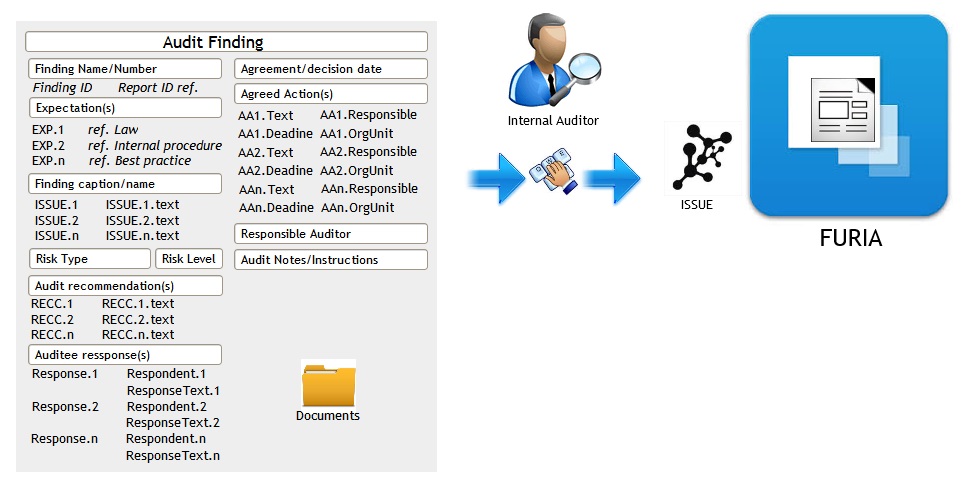
Unlike dedicated solutions available for the audit management, FURIA do not force you to define unnecessary fields and allows you to define the finding-atom just as it is in your company, not more or less. So, again, application will not “force” any changes on your audit management process that you don’t really want. One by one, findings are entered until you enter them all. Also, customers have option to require bulk-inserting the large number of the reports and the issues in a automated process, e.g. if your Group consists of 10+ companies or 50+ franchises, don’t worry about time necessary for mass imports. Mass imports can be done by our support team or can be designed as continuous process that will execute your Audit or IT staff.
Then you set the permissions in accordance to least privilege access rule. Information encapsulation assure that every auditee can see and interact only with the Findings where he is marked as direct responsible, or on these issues where he/she is added via use of delegated access functionality. Another important thing is inheritance of access level, so Director of Retail sector can access and interact with all the findings related to his sector and all the division withing that sector, but not the other sectors – they remain invisible to that Director.
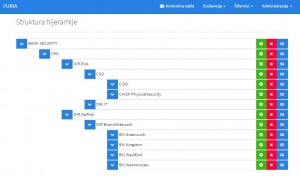
Example of one finding delegation:
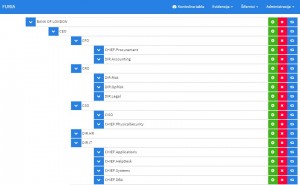
All these permissions and relations are defined in Hierarchy structure that is applied for the Audit atoms. However, it is available option to create unlimited number of internal Hierarchies. That way, you can define Hierarchy of internal audit reports and findings, but you can also define complete new Hierarchy for Audit Reports made by External Auditors, or reports related to National Bank controls. This way the company is assured that nobody can reach point of unauthorized access to sensitive information.
Two examples different types of atoms and their correspondent Hierarchy structures, one used for Audit Management and the second used for Security Issues Management in FURIA system:
Now, the Audit Report and its Findings are ready for publishing. Involved parties (auditors, audit supervisors, auditee and others in the Hierarchy tree) receive notification about new report that is just published and become available to the “audience”. From that moment on, all parties can interact the findings in accordance with set privileges and responsibilities.
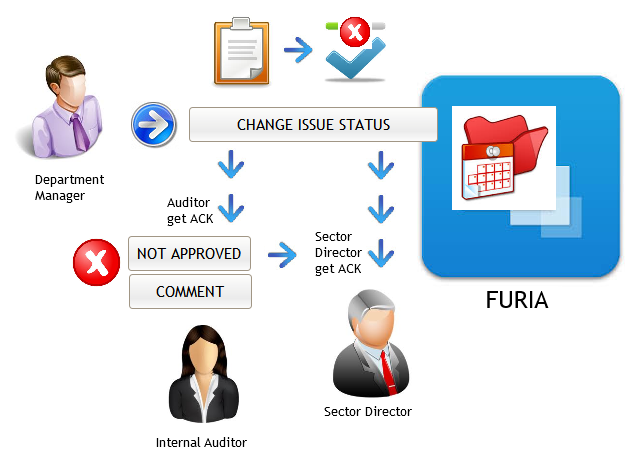
Responsible auditee can interact the findings for the changes of the finding status, can post the management comments (e.g. giving feedback about implementation progress) and upload relevant documents.
Each action is supervised by auditors in charge of the particular Audit Report and each individual Finding. Each change should be approved or rejected by auditor in charge. On one single report you can delegate authority to several auditors where none of them can interfere with the each other responsibility – e.g. auditor that is tax-specialist will supervise tax-related findings, information security auditor will deal with particular technical findings, and so on.
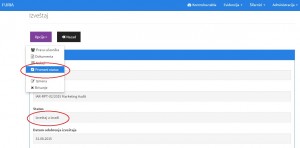
Options for publishing the audit report being prepared in FURIA:
Process of change approval, simplified:
This way, sensitive information encapsulation is preserved even within the Audit Department, e.g. junior auditors cannot access the data that are not allowed to see or use, while they are allowed to access few particular findings that CAE delegate to them. So, the same principle of least privilege access is easily applied within the Audit Department among different auditors, just as it case with segregation and encapsulation of information on the auditee side.
Each change made to the particular Finding is automatically available for all the parties upon supervisory approval (e.g. in case of status change) or directly (e.g. posting new comments as Management Response for quarterly Audit Follow-Up report for Audit Committees).
There are several status stages that Audit Finding and Audit Report is passing, from publishing to completion. It can be also cancelled, which is supervised by responsible Auditor and CAE. Closing of the Audit Finding is point where Auditee change the status to Closed and post the relevant comment with relevant document as supporting evidence that the case is really closed.
Once when the all Audit Findings in one Audit Report are completed, the Audit Report change its status to completed. Then, the whole structure can be archived if your Audit Follow-Up procedure don’t require statistics on past things, or it can continue to live as locked data, something that cannot be altered afterwards.
Typical initial setup of FURIA system in the banks and insurance companies assume one uniform Hierarchy with three types of atoms: Internal Audit, External Audit and Regulatory Control/Audit Reports. The main reasons to apply three instead of one model is segregation of duties and strong limitation of access to sensitive information.
For the non-banking sector, usual case is that Internal Control reports are available with one Hierarchy. Of course, this is the choice of the customer and it can always be changed in accordance with requirements.
Comprehensive reporting system enables all the parties to have clear insight in progress of agreed actions implementation, preserving security limitations that are already applied in process. Customization of access controls can grant reporting permissions for parties that are involved for specific tasks, such as preparing reports for e.g. monthly Audit Committees, quarterly or annual Shareholders Assembly, etc.